Google revealed in 2020 that more than 2 million developers have used flutter since its release in 2018, making it one of the most popular frameworks on the market today. In the beginning, flutter was only available as an Android and iOS mobile application development framework, but now that we have flutter desktop and flutter web released, the framework has just become even more popular among flutter developers.
Our main concern is writing code and adding new features, so we don’t always focus on making sure everything in our application is secure and robust. This is due to our focus on writing code and creating new features rather than ensuring everything is secure and robust.
Now this can cause an issue when you are putting your application into deployment after after everything is done and tested and you are putting it out for production that can leave the application vulnerable to attacks which can cause user data leaks it can result in your application business logic being exposed or it can even cause your data and or your API keys and your resources misused, which in turn can be very costly especial you’re reaching out and using something like Firebase or you know AWS.
There are a few steps that we can take to secure our Flutter applications in this article let’s have a look at Eight such steps which you can take to make sure that your next Flutter application is completely secure and robust.
1) Obfuscate code
So the first thing that we’ll look at to make your Flutter applications more secure is code off escalation. Now what is code obfuscation?
Obfuscation is a technique used to make code harder to understand for reverse engineering purposes. When you have an APK file in Android, you can extract its contents and view the code written in Java files. Obfuscation doesn’t change the code itself but rather modifies the names of variables, classes, and other elements. This makes it more difficult for humans to understand the code. Its purpose is to protect the code from being easily understood by unauthorized individuals.
This is a very generic term in the software industry. The purpose of this is to make your app’s binary harder to understand for humans.

You can reverse engineer a Flutter application or an Android application so that it generates and provides information like function names, class names, and strings in the application. Because it exposes so many different details, your API keys are exposed as well.
It puts a safeguard against reverse engineering if they are not managed properly or if your business logic is exposed by your class and function names.
for more info checkout here
2) background snapshots
In order to continue with the second step, the operating system takes a snapshot when the app is in the background, so the large state is saved when the application is in the background.
so when you when you when your app is minimised and you know rolling around in into your other apps so the snapshot of the last screen that you are standing on goes along with the minimised version so you see like this you can see blow the screen how to secure them for suppose you have some card details here and then you minimise your app and then somebody scrolls in your minimised apps and then you he can see the the card details and stuff like that so how do you secure that so there are simple two three line codes which you can put in native android and native iOS in order to stop this.
For example, the clock app and the calendar app both have snapshots, so correspondingly, we have snapshots for both of them, so this is a good feature, but it’s not ideal if you have any private information.

The best example of this is Google Pay, so if you go to the app and start typing in your bank account details or transferring money to someone, then you open the application in the background, and then you see that the screen changes to white, which is the content of the tab that hides the app.
In this way, we can go ahead and implement a particular plugin if there is some sensitive information in our application that we do not want to show in the background.
3) Stay up-to-date
Therefore, the third point is very important to remember whenever you are starting a new Flutter application. The updated version should be your starting point.
Keeping your Flutter SDK, plugins, and packages up-to-date is one of the easiest and best ways to secure your apps. As security vulnerabilities are discovered in the Flutter framework, Google releases patches and security fixes.
Identify any unresolved issues that haven’t yet been filed on the Google Flutter repository, and report them.
4) Flushing in-memory cache
Fourthly, if you are building something very critical and very secure like banking apps, you should flush your in-memory cache as often as possible. In any mobile development technology, flutter is the most secure way of storing something that comes to you from a back end or a database, which is why it is in memory the most secure way.

This is because it’s generated at runtime and stored in a runtime variable that gets cleared when the app is killed, so it’s not stored anywhere. It’s fetched on a runtime and stored in a runtime variable.
Data or tokens or anything like that should be stored in memory, in the variables that you use in your app.
Alternatively, if you would like to add an extra layer of security, you can use this small code that you can see right now here to flush your memory after a certain time. For example, if i am using a banking application and my app goes to background and I am using another application.
Because the app is running in the background for like 15 minutes or 20 minutes, it might be vulnerable to other apps or scripts reading your memory variables.
After two minutes or three minutes of inactivity, you’re going to be able to flush your in-memory cache, so this code actually tells you when the app is paused, so you just check for 15 minutes and then clear it.
5) local authentication
next thing in connection with this is usually local authentication.when you have a snapshot implementation in place, it is usually desirable to make the user authenticate locally again when you open the snapshot again.
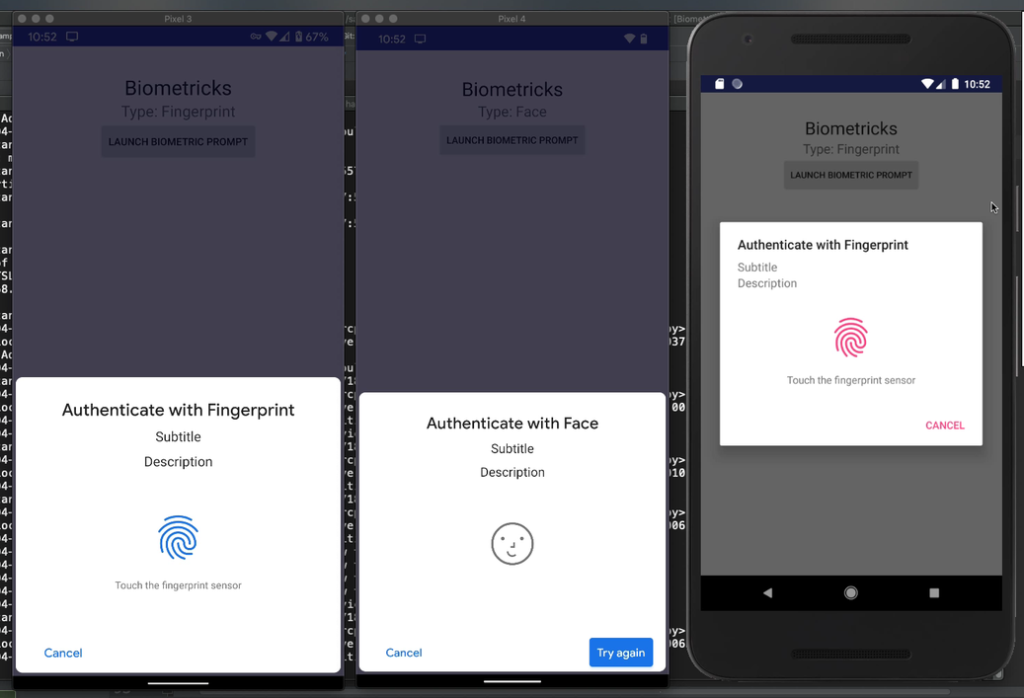
By local authentication, I mean bio-metrics, facial recognition, or something similar, so if you look at whats-app, you can add a fingerprint lock, so we can do something similar for our app.
Whenever the application returns from the background or is opened for the first time, we authenticate the user locally in order to make sure that they are valid, so this is also very useful for users who have payment information or know sensitive information, such as social media information.
You cannot fetch the signatures of those that are restricted by OS because that is identity theft, and the OS doesn’t allow you to do that either. When you check for fingerprints, the OS only tells you whether the fingerprints are true or false. That’s the only thing you get from it.
6) Secure Storage
Secure storage is next, so if you’re using shared preferences or a sqlite database the plugin you’ll need is called sqflite if you’re using this.

As a result, shared preferences are a part of your app that keeps your data persistent even after you kill it. You should not store plain passwords or pins in your shared preferences because they can be read by other apps through code and they can also be cleared by the user themselves, so you shouldn’t store straight plane passwords or pins in your shared preferences.
Even if you want to store something that is critical to you and your shared preferences, you should use encryption and encrypt it before storing it.
Even if you know you are being exploited, your shared preferences won’t be affected, so you can keep things like theme data or tokens that get the user data from the back end or tokens that tell you whether the app has been installed for the first time or things like that. It is the things that you want to keep to ensure the app persists.
We need to ensure that our data is safe and encrypted, so we can use flutter secure storage, which is a plugin that makes use of key-chain and AES encryption for Android. Thus, we make sure that the data we are storing locally is also encrypted and safe, so that’s another way to increase the security of your android application.
for this you can prefer this plugin
7) Restrict network traffic
So Seventh point is Restrict network traffic, Network Traffic Control offers internet connectivity barrier, either to its own servers or to third-party vendors. To provide a secure connection between your mobile applications and your servers, information is normally exchanged via a Transport Secure Layer (T.L.S).
The most trusted network
In order to restrict network traffic or connection to an unsecured endpoint, you can explicitly whitelist your domain.
For Android:
res/xml/network_security_config.xml
<?xml version="1.0" encoding="utf-8"?>
<network-security-config>
<domain-config>
<domain includeSubdomains="true">yourDomain.com</domain>
<trust-anchors>
<certificates src="@raw/my_ca"/>
</trust-anchors>
</domain-config>
</network-security-config>For iOS:
ios/Info.plist
<key>NSAppTransportSecurity</key>
<dict>
<key>NSAllowsArbitraryLoads</key>
<false/>
<key>NSExceptionDomains</key>
<dict>
<key>cocoacasts.com</key>
<dict>
<key>NSIncludesSubdomains</key>
<true/>
<key>NSExceptionAllowsInsecureHTTPLoads</key>
<true/>
</dict>
</dict>
</dict>8) jail-breaking protection
Last but not least, we have jail-breaking protection. In order to define the term jail-breaking, it’s actually a term associated with iOS systems. In jail-breaking, you root your iOS device so that you can actually access, you know, revoke, or even tamper with, any restrictions Apple has imposed.
In case of Android, you would actually be going into developer mode when you were you know changing your device in general, so that you could install third-party applications or do all sorts of changes. Although sometimes this state is useful, it isn’t always malicious, so the device will still have a state of this kind whenever it is used.
Your application or its data might be affected by some malware that was introduced with the device. If you want you can check for such malware.

In such a case, you can detect the device’s state and take appropriate actions. For instance, if you have routes in your application that you want to restrict for jail-broken or rooted devices, you can restrict them.
There is nothing secure in this world. If I create an app today it may be secure for today, but in two days, three days, or after a year it might not be secure.
In other words, I can create an app that is secure today, but it may not be secure tomorrow, so there is no such thing as an application that is 100 percent secure.
So, here are the Eight steps to make your application more secure and robust. It is impossible to guarantee that your application will always be foolproof, but adding those eight steps will certainly enhance your chances.
So that’s all the information that helps us for creating Secure Your Flutter Mobile Applications, that I want to describe in short. I took it from many websites as some research if you find out any wrong info or misdirected, please point it out or comment below.